- 11 Apr 2024
- Print
- DarkLight
- PDF
Findings
- Updated on 11 Apr 2024
- Print
- DarkLight
- PDF
Overview
Findings are the vulnerabilities that are collected from your tools and presented in Seemplicity. The Findings that are presented are based on the Scope and Filter that you select, and after they have been normalized, de-duplicated, and aggregated.
For example, you can see below that for the scope called Demo.com, Seemplicity is presenting 17,380 Findings. However, these Findings are derived from 24,685 Findings that were collected from your various tools. That's about 30% less individual tickets that your team would have to manage.
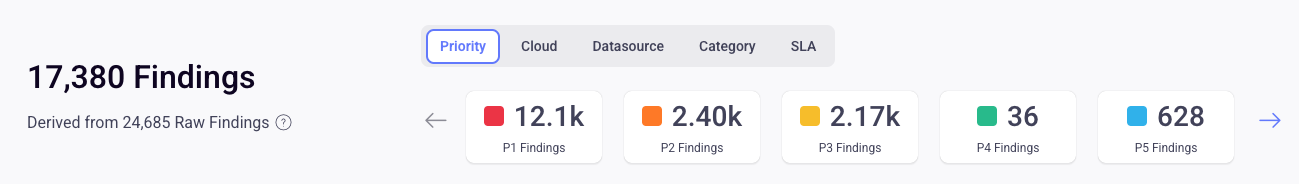
The main Findings page provides you with a high-level view of your Findings, what their statuses are, how many resources are included in a given Finding, and more. For example, you can see that the selected Finding applies to 682 resources.
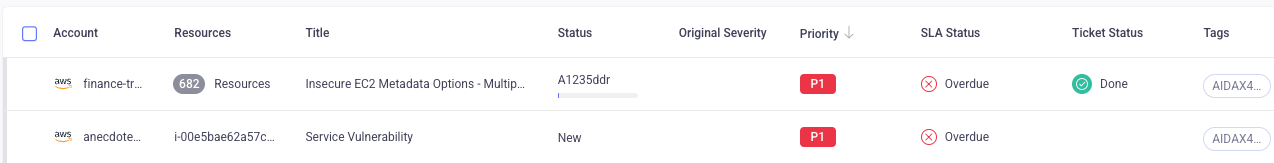
The following sections explain how Seemplicity processes the Findings to present a more accurate and manageable view of your security posture.
If you'd like to jump ahead to how to get operational with the table, see this topic on how to use the Findings table as a tool.
Step 1: Normalization
Normalization is the process of taking Findings from the different Data Sources and recalibrating them so the information is presented in a uniform manner. For example, one Data Source might have a severity field, while another would have importance, and yet a third would have priority.
In addition, each of these fields might score the data differently. So, the Data Source using severity might use a score ranging from 1 to 100, while the Data Source using priority is using high, medium, and low.
Seemplicity takes these different definitions and normalizes them so they are presented and formatted consistently throughout.
Step 2: De-duplication and Aggregation
Seemplicity identifies duplicate items that are ingested from the multiple Data Sources you are using and combines them into a single item. In addition, Seemplicity is able to take multiple Findings with the same solution and aggregate them into one solution.
For example, if you have multiple vulnerabilities identified by one or more Data Sources, that are resolved by one solution, e.g. a Microsoft patch, the vulnerabilities display in Seemplicity as one Finding.
This one Finding is translated into an action item that needs to be resolved, and as that resolution takes place, the Finding is updated accordingly. In addition, this Finding can also be translated into 1 ticket in your ticketing system for the relevant team, which decreases the noise/volume for them.
Actions
After you've reviewed the results, from the main Findings page, you can perform several bulk actions. You can download a CSV file of all the results in the Findings table (see also Download Manager), change status and priority of multiple findings, aggregate according to a previously configured rule, create tickets in your selected ticketing systems, create a manual finding (for details, see Manual Findings), or complete a bulk upload of ticket information from another source.
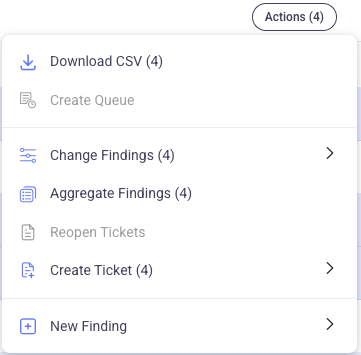
You can manually aggregate several findings into a single finding in the event that you determine they should be managed as one single item.
Findings that have already been aggregated, cannot be included in a manual aggregation.
Workflow: Understanding Findings Data
When you drill down into a specific finding, you will see more detailed information, including how you can remediate it, the Resources that were affected and more. You can also perform various manual actions for the specific finding.
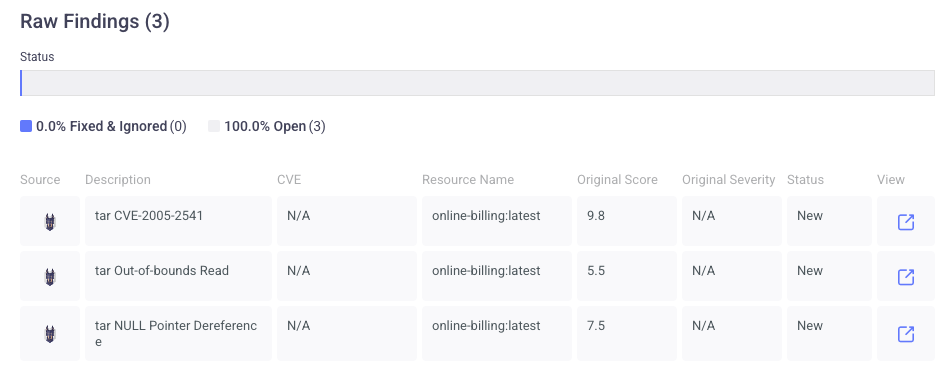
For example, we can see that the following finding is a vulnerability discovered by Snyk for a tar that must upgraded. This is a Priority One level Finding, and we also see that this was discovered on one resource in the organization.
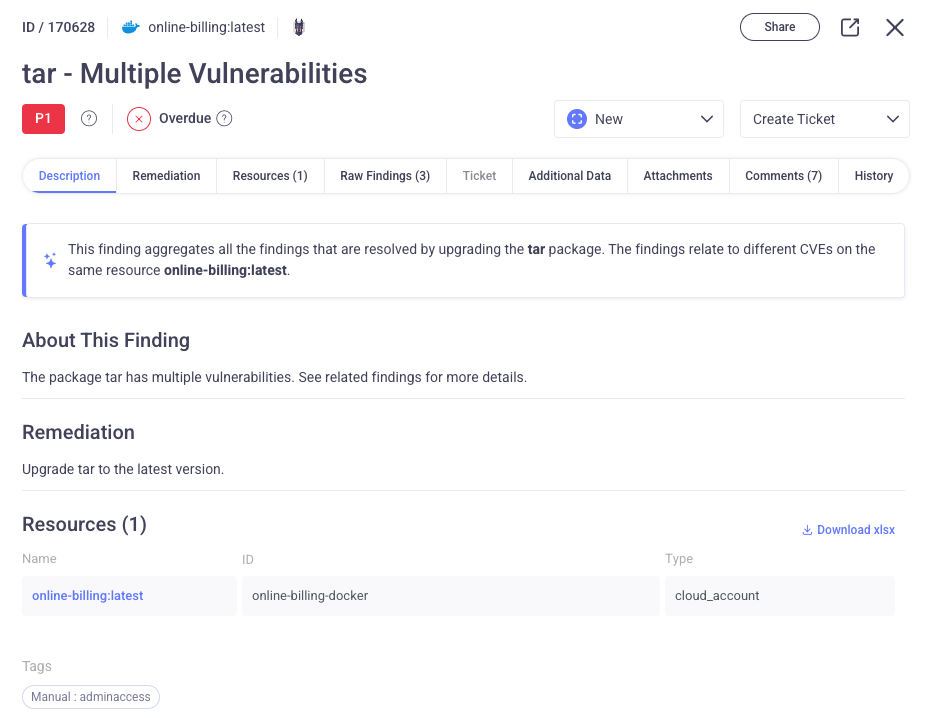
In fact, this Finding is comprised of three different CVEs. But, as we see from the Remediation section, updating the one tar file will resolve all three issues at once.

Remediate the Finding
Knowing what we now know, we can manually create a Ticket from within this Finding, which will include all of the relevant information for the respective team that needs to apply the fix.
After each subsequent scan by Snyk, the finding is updated showing us which Assets are no longer exposed, if any new machines were added, and more.
We can also add attachments or comments to help communicate information to additional team members, ask questions, etc.
Change Finding Status
You can change the status of a finding to reflect its progress, change to a false positive, or add an exception.
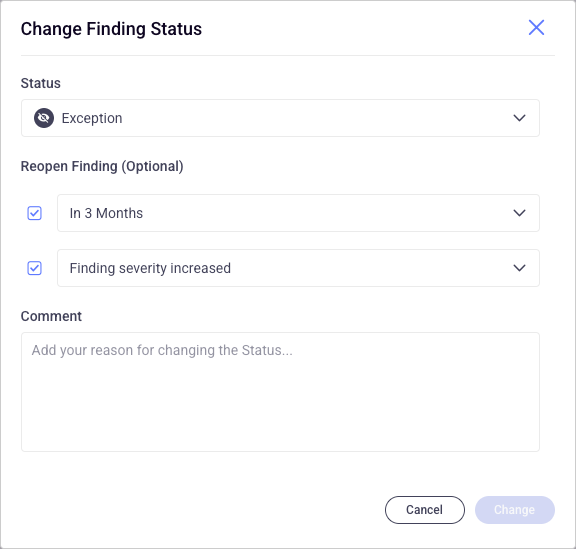
For example, if the team responsible for the item has determined that the Finding should be an exception, you can determine for how long, or under which circumstances this exception needs to be revisited. In the example above, we created an exception and determined that it should be checked again either in three months' time, or in the event that the severity increases.
Using the Findings table as a tool
From the Findings screen, you can view your data from different angles to fit your team's needs. For details, see Operationalizing the Findings Table.
